Study of the Key Reinstallation Attacks (KRACK) Vulnerability
Info: 2032 words (8 pages) Study
Last Edited: 29th Aug 2022 by David Norman
Abstract
This study's objective is to investigate the Key Reinstallation Attacks (KRACK) vulnerability related with Wireless Fidelity (Wi-Fi) networks and the Wi-Fi Protected Access 2 (WPA2) protocol. Wi-Fi is a wireless technology that links local client devices to the internet. WPA2 is a protocol that maintains security through client and access point authentication.
Introduction
The Institute of Electrical and Electronics Engineers (IEEE) 802.11 standard outlines the parameters of a wireless local area network (WLAN). In simple terms, this means they regulate how data transmissions are sent over a network. A WLAN can be built using 802.11 Wi-Fi standards. This protocol allows the client station (STA) – for example, a laptop or mobile phone – to connect to an access point (AP) which then connects to the internet. An AP uses radio frequency waves to propagate the signal to the STA. A limitation with Wi-Fi is that the range from the AP to the STA can be very short. Another negative is that it is easier to exploit a WLAN, so an authentication protocol is needed.
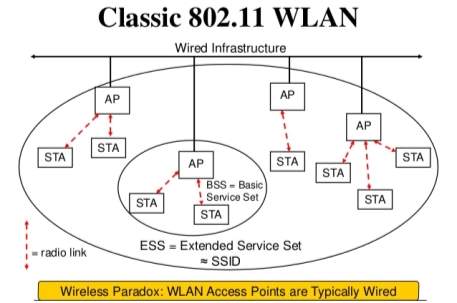
(802.11 WLAN, n.d.)
Wi-Fi Protected Access 2 (WPA2) protocol is a type of encryption which uses a 4-way handshake to securely connect the client to the WLAN. A WPA2 protocol gives unique encryption keys to every wireless STA that connects to it. WPA2 certification was given by Wi-Fi Alliance to mirror IEEE 802.11. WPA2 has backwards compatibility with WPA and supports both the WPA2-PSK (Pre-Shared key) and WPA2-Enterprise. WPA2-PSK is a security protocol that is designed to be used on a network with a few trusted STAs, this is because it only requires one password. WPA2-Enterprise is an encryption protocol designed for businesses and uses a Remote Authentication Dial-In User Service (RADIUS) server, this provides external authentication meaning the AP acts as the intermediary not the authenticator in WPA2-Enterprise. This extra security prevents dictionary attacks on authentication. January 2018 Wi-Fi Alliance announced that WPA3 was
Key Reinstallation Attack
A Key reinstallation attack is the technique where the attacker tricks the STA into reinstalling a previously used key to gain access to the network. KRACK exploits both WPA and WPA2 protocols 4- way handshake. The 4-way handshake starts by confirming the AP and the STA have the same pre-shared key (PSK) for the network. The AP and STA can do this without ever disclosing the PSK by sending an encryption that can only be decrypted if the recipient has the PSK. The way they do this is the AP send a number used once (Nonce) to the STA. A nonce is used in cryptographic communications to prevent replay attacks. The AP also send a key replay counter, the purpose of this is so that the AP can identify messages its receives from STAs match the nonce it has sent out.
The STA will receive message 1 from the AP and using the PSK can create its own nonce value this will be sent along with the key replay counter from message 1 so that the AP can identify the authentication key and a message integrity code (MIC) this is a personal code that checks for tampering of the message. While the STA is doing all that it will also create a Pairwise Transient Key (PTK). PTK is a key that is generated from the Authenticator Nonce (ANonce) from the AP, Supplicant Nonce (SNonce) from the STA, PMK, AP media access control (MAC) address, STA MAC address. The PTK is then used to encrypt all unicast transmissions between the STA and the AP.
Once the AP has received message 2 it verifies the ANonce, MIC and Replay counter if this is authenticated then sends the STA a MIC and a Group Temporal Key (GTK) this is a key that can be used if the AP broadcasts to the whole network or multicasts to more than on STAs on the network.
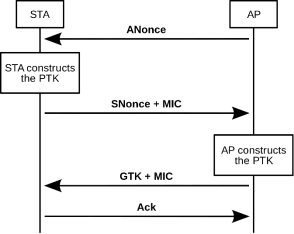
(The four-way handshake in 802.11i, 2018)
When performing the KRACK process the attacker will get the client to reinstall a previously used encryption key. The way the attacker can achieve this is through collecting and replaying retransmissions of messages 3 and 4. KRACK is a type of replay attack, this is where the hacker intercepts an encrypted message and then resends it. As its already an authentic message then the receiver believes it to be genuine.
“However, because messages may be lost or dropped, the Access Point (AP) will retransmit message 3 if it did not receive an appropriate response as acknowledgment. As a result, the client may receive message 3 multiple times. Each time it receives this message, it will reinstall the same encryption key, and thereby reset the incremental transmit packet number (nonce) and receive replay counter used by the encryption protocol. We show that an attacker can force these nonce resets by collecting and replaying retransmissions of message 3 of the 4-way handshake. We show that an attacker can force these nonce resets by collecting and replaying retransmissions of message 3 of the 4-way handshake.” (Vanhoef, 2017)
A successful KRACK could mean the attacker can read HTTP (Hypertext Transfer Protocol). This is an unencrypted language that is used to write websites, a consequence of this could be the attacker would be able to add malicious data to websites that the victim uses often. Furthermore, the attacker would have the ability to decrypt data packets and therefore have access to the targets personal data this could include; passwords, emails and bank details. HTTPS is now in widely in use. The ‘S’ stands for secure and the difference that HTTPS is encrypted.
A limitation when carrying out the attack is that hacker needs to be within range of the client device and the Wi-Fi network. However, the attacker might not be as close as you might think.
“That’s because special antenna can be used to carry out the attack from two miles to up to eight miles in ideal conditions. Additionally, the attacker is not competing with the signal strength of the real Wi-Fi network, but instead uses so-called Channel Switch Announcements to manipulate and attack the client. As a result, it is possible to successfully carry out attacks even when far away from the victim.” (Vanhoef, 2017)
Common software tools that are used in wireless attacks are as follows;
- Aircrack-ng – this is a command line tool compatible with; Windows, Linux and OS X. Aircrack-ng is used to attack wireless networks by collecting packets until it has enough packets to recover the password.
- AirSnort – Performs packet capturing until it can decrypt keys. Compatible with Windows and Linux.
- Cain and Abel – A very popular password cracking tool that can sniff a network and perform cryptanalysis attacks.
- CoWPAtty – Command line tool used to attack PSK on WPA networks. Can also perform dictionary attacks.
- Airjack – this tool is used to capture and then alter packets, so it can then perform a denial of service attack by inserting the dirty packets back onto the network.
- Fern Wifi Cracker – is used against WEP and WPA networks by performing brute force attacks and can save the keys of successful attacks on a database.
- NetStumbler – Windows tool used to find rouge APs, network mis-configurations and poor connectivity areas.
- Wireshark – A network analysing tool that allows you to look at the traffic flowing through your network.
Related Common Vulnerabilities and Exposures listed in the national vulnerability database:
- CVE-2017-13077: Reinstallation of the pairwise encryption key (PTK-TK) in the 4-way handshake.
- CVE-2017-13078: Reinstallation of the group key (GTK) in the 4-way handshake.
- CVE-2017-13079: Reinstallation of the integrity group key (IGTK) in the 4-way handshake.
- CVE-2017-13080: Reinstallation of the group key (GTK) in the group key handshake.
- CVE-2017-13081: Reinstallation of the integrity group key (IGTK) in the group key handshake.
- CVE-2017-13082: Accepting a retransmitted Fast BSS Transition (FT) Reassociation Request and reinstalling the pairwise encryption key (PTK – TK) while processing it.
- CVE-2017-13084: Reinstallation of the STK key in the PeerKey handshake.
- CVE-2017-13086: reinstallation of the Tunneled Direct-Link Setup (TDLS) PeerKey (TPK) key in the TDLS handshake.
- CVE-2017-13087: reinstallation of the group key (GTK) when processing a Wireless Network Management (WNM) Sleep Mode Response frame.
- CVE-2017-13088: reinstallation of the integrity group key (IGTK) when processing a Wireless Network Management (WNM) Sleep Mode Response frame.
Conclusion and Future Work
Having reviewed my research I believe while KRACK is a genuine threat to WPA/WPA2 it is a very low risk that can be mitigated by carrying out a few simple things such as; only accessing websites that use HTTPS, avoid using public Wi-Fi, using a Virtual Private Network (VPN), avoid doing sensitive things on the internet such as internet banking.
References
- Burgess, M. (2018). The Krack vulnerability is another good reason to ditch public Wi-Fi. [online] Wired.co.uk. Available at: https://www.wired.co.uk/article/krack-update-patch-wifi-apple-google-sky-bt-virgin-talktalk-public-wifi [Accessed 11 Dec. 2018].
- Us.norton.com. (2018). What you need to do about the WPA2 Wi-Fi network vulnerability. [online] Available at: https://us.norton.com/internetsecurity-emerging-threats-what-to-do-about-krack-vulnerability.html [Accessed 13 Dec. 2018].
- Kelly, G. (2018). 802.11ac vs 802.11n WiFi: What’s The Difference?. [online] Forbes.com. Available at: https://www.forbes.com/sites/gordonkelly/2014/12/30/802-11ac-vs-802-11n-wifi-whats-the-difference/#65fac9af3957 [Accessed 8 Dec. 2018].
- Fehér, D. and Sandor, B. (2018). Effects of the WPA2 KRACK Attack in Real Environment – IEEE Conference Publication. [online] Ieeexplore.ieee.org. Available at: https://ieeexplore.ieee.org/document/8524769 [Accessed 14 Dec. 2018].
- Nvd.nist.gov. (2018). NVD – Results. [online] Available at: https://nvd.nist.gov/vuln/search/results?form_type=Basic&results_type=overview&query=KRACK&search_type=all [Accessed 12 Dec. 2018].
- Vanhoef, M. (2017). KRACK Attacks: Breaking WPA2. [online] Krackattacks.com. Available at: https://www.krackattacks.com/ [Accessed 12 Dec. 2018].
- The four-way handshake in 802.11i. (2018). [image] Available at: https://en.wikipedia.org/wiki/IEEE_802.11i-2004#/media/File:4-way-handshake.svg [Accessed 11 Dec. 2018].
- 802.11 WLAN. (n.d.). [image] Available at: https://image.slidesharecdn.com/ieee802-140411111057-phpapp01/95/ieee-80211s-tutorial-overview-of-the-amendment-for-wireless-local-area-mesh-networking-6-638.jpg?cb=1397214791 [Accessed 10 Dec. 2018].
Cite This Article
To export a reference to this publication please select a referencing stye below: